As word of the Heartbleed bug spread across the Internet, IT professionals across all industries have taken notice and are working tirelessly to resolve the issue. Public health officials, health care administrators and privacy advocates are concerned about the potential security implications for patients and medical providers, especially given the sensitivity of patient data such as Social Security numbers or treatment information.
According to Healthcare IT News, Phil Lerner, the chief information security officer at Beth Israel Deaconess Medical Center in Boston, says responding to the bug is a high priority, ranking it a 7.5 on a scale from 1 to 10.
What Is the Heartbleed Bug?
 The Heartbleed bug is a vulnerability in OpenSSL, the encryption software used by an estimated two-thirds of websites and in some gadgets such as servers, routers, and video cameras. Tech companies Cisco and Juniper have revealed that several of their products may have been compromised. Countless other companies are scrambling to respond to customer concerns and deploy Fixed Open SSL.
The Heartbleed bug is a vulnerability in OpenSSL, the encryption software used by an estimated two-thirds of websites and in some gadgets such as servers, routers, and video cameras. Tech companies Cisco and Juniper have revealed that several of their products may have been compromised. Countless other companies are scrambling to respond to customer concerns and deploy Fixed Open SSL.
The vulnerability has existed for at least two years, but its existence has only recently come to light. The bug allows attackers to eavesdrop on online communication, steal data and impersonate other users and services, all without being detected. International IT security company Secunia warns that removing the bug from computers and gadgets could take months. Even Health IT giants like Healthcare.gov may be vulnerable: users were recently advised to change their passwords as a safeguard against the bug:
https://www.youtube.com/watch?v=zTCEfs5Q-kI
How Could Heartbleed Affect the Security of Health Organizations?
According to Modern Healthcare, the bug could compromise any websites that have a built-in encryption capability, such as provider websites, physician and patient portals and remote access systems. The HIPAA Security Rule requires that covered entities and their business associates implement appropriate administrative, physical and technical safeguards to protect electronic health information.
If a medical practice has weaknesses in these areas, the practice may need to report a breach to the patient and federal Health & Human Services (HHS), which now has a searchable online database of breaches impacting 500 or more people. They may also need to notify patients about the breach, and this news can cause issues with patient trust, not to mention the other costs involved.
One website estimates that the costs of notifying patients via email, mail or other means can run into the millions of dollars depending on the size of the breach. Some medical practices also provide free credit monitoring or identity theft protection to affected patients following a data breach.
What Steps Can Administrators Take to Protect Patient Data?
The Texas Medical Liability Trust suggests that medical practices take proactive steps to assess potential vulnerabilities relating to the Heartbleed bug as soon as possible. As they’re performing these tasks, administrators should document each step to show that they’re following best practices in case of future issues or audits.
McAfee has released a free Heartbleed test tool where users can enter a URL or IP address to see if the websites they use have upgraded to Fixed Open SSL or are not using SSL. IT professionals can also check with their vendor or hosting services to find out if their websites, scheduling sites or other systems have been impacted by Heartbleed and if their SSL has been updated.
It’s also important to make sure that each employee’s computer or tablet has up-to-date anti-virus and malware software with security patches installed on a regular basis. Each computer should also have up-to-date web browsers.
Employees should not use the same passwords on multiple platforms or websites because if a password is compromised on one, it could compromise security on another. Health administrators should encourage employees to use multiple passwords and to update them often using a combination of letters, numbers and special characters.
What Can We Learn from Past Breaches?
Given the emerging nature of health care IT as a field, Heartbleed and other breaches pose unique and complex challenges. However, this is not the first time that medical data security has been compromised. As medical records go digital and move away from the traditional paper files, health care administrators have increasingly wrestled with the threat of data breaches.
An HHS database shows that many medical data breaches involve portable hardware devices such as laptops or drive drives. Securing these devices or storing the information in the cloud with secure passwords and encryption may help prevent many of these breaches (although it wouldn’t necessarily protect against the Heartbleed bug).
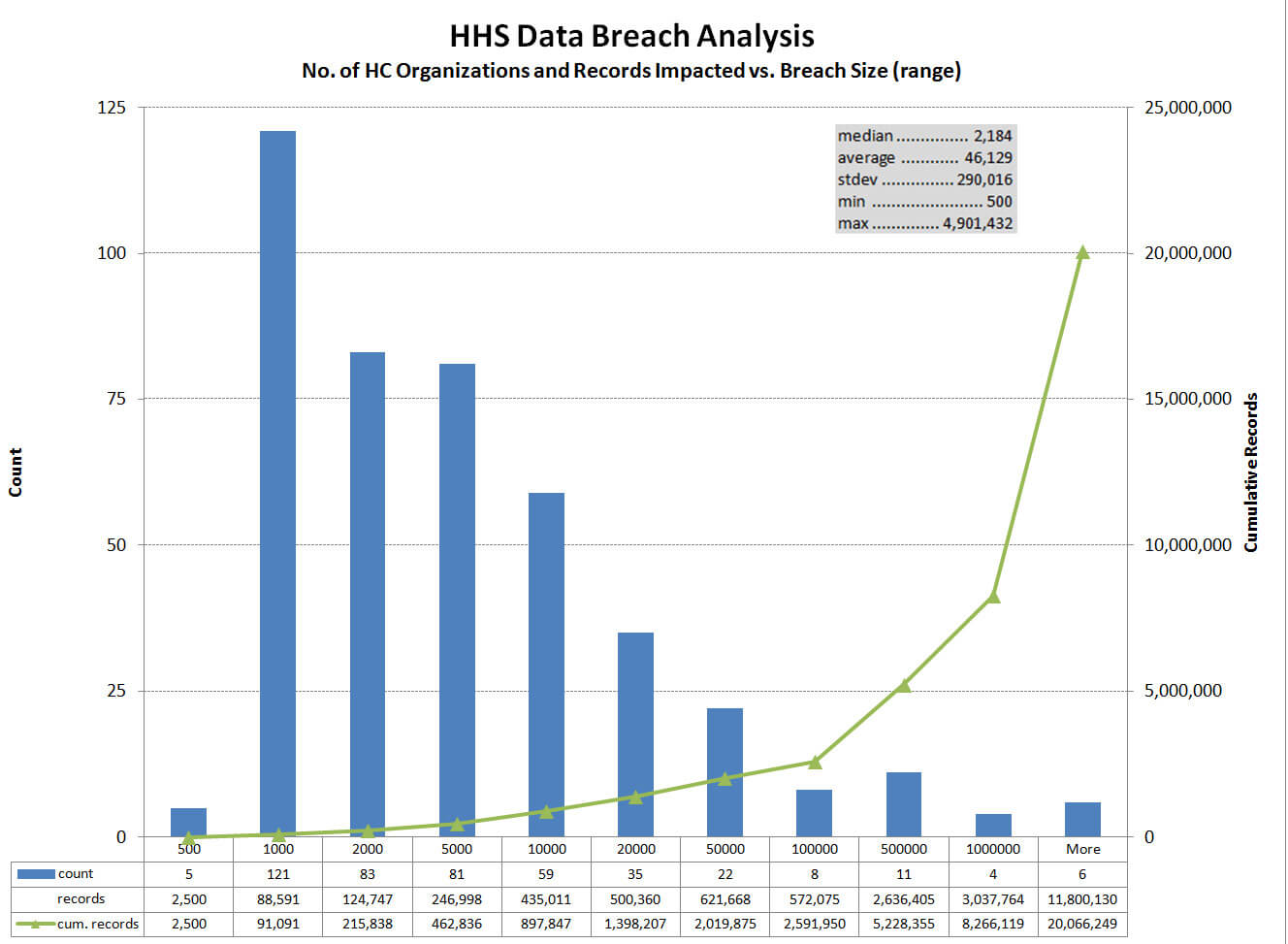
Largest Medical Breaches since 2009
Click image to enlarge
Image courtesy of: lumension.com
TRICARE
The largest medical data breach since the HHS began tracking incidents in 2009 involved TRICARE, which provides civilian health benefits for military personnel, military retirees and their families. Nearly five million patients had their information compromised when TRICARE’s backup computer tapes for electronic health records were stolen from the car of one of its business associates.
Howard University Breach
Kaiser Health News reports that in 2012, Howard University Hospital had the medical data of more than 34,000 patients compromised after a contractor downloaded patients’ files onto a personal laptop and had the laptop stolen. That same year, federal prosecutors charged a medical technician at the hospital with violating HIPAA to obtain and sell patients’ names, addresses and Medicare numbers.
According to the U.S. Attorney’s Office for District of Columbia, the former employee sold blank hospital prescription forms and the information for about 40 patients, receiving $2,100 cash in return. The employee pled guilty and was sentenced to six months in a halfway house and 100 hours of community service.
UnityPoint Health
The Sioux City Journal reports that in 2013, UnityPoint Health of West Des Moines, Iowa, reported that unauthorized access to its electronic health records system put as many as 1,800 patients’ data at risk. A third-party contractor is believed to have inappropriately accessed patient information such as names, addresses, and health insurance account numbers.
Also in 2013, Advocate Medical Group notified roughly four million patients after four computers were stolen from an administrative office in Park Ridge, Illinois. These are just a few examples of data issues plaguing the health care industry, as administrators work to comply with digital records requirements and implement strategies for safeguarding that information.
While the full impact and resolution of the Heartbleed bug remain to be seen, health care administrators will be working diligently to strengthen security practices and ensure that patient data is better protected in the future.
Conclusion:
What are your thoughts about protecting your organization, is your staff properly trained and ready for issues relating to security and data breaches?
Let us know what you think in the comment section below.